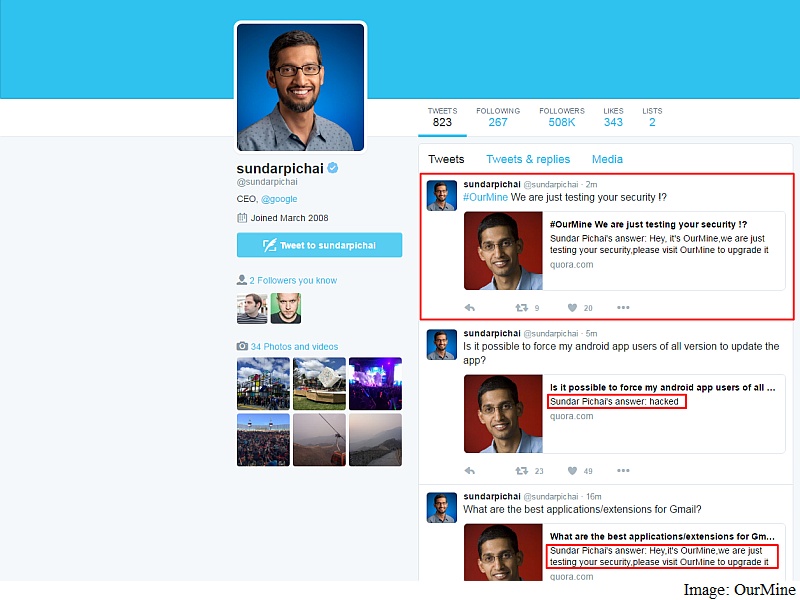
Hello, friends here is a good news that there are about 10.9 million apps which are available on about 200 app stores (from where we download apps for our smartphones. And the bad news is that a third of them about 3.4 million apps comes with malware in it, which can steal data, contacts, passwords, personal information (bank accounts etc.) and can cause much more harm to your smartphone.
There are about two third of people in India are accessing the internet nowadays through their smartphones. This shows how it is vulnerable to cyber attacks which take place in India.
The latest survey by Internet security solutions firm Symantec’s Internet Security Threat Report indicates that dependency on mobile devices has gone up significantly in the last two years as mobile penetration increased significantly.
“The survey, conducted in 14 Indian cities in May, shows that people are checking the mobiles at least 41 times a day,” Ritesh Chopra, Country Manager (India) of Symantec told Business Line.
About 50 percent of people have 20 apps in their phones in which about 5 are mobile wallets and e-commerce apps which they use for their business and commercial purpose. People are unwittingly giving permissions to unknown and unverified developers to download apps. A good no. of apps are fake and can steal all this information and data from your phone and can make your life miserable
There are a lot of cyber crime cases takes place nowadays in India. And half of them takes place from phones.
CONCLUSION: SO, THIS IS NECESSARY TO ONLY DOWNLOAD THOSE APPS WHOM YOU TRUST AND NOT GIVE PERMISSIONS TO UNKNOWN AND UNVERIFIED DEVELOPERS TO DOWNLOAD APPS.
There are about two third of people in India are accessing the internet nowadays through their smartphones. This shows how it is vulnerable to cyber attacks which take place in India.
The latest survey by Internet security solutions firm Symantec’s Internet Security Threat Report indicates that dependency on mobile devices has gone up significantly in the last two years as mobile penetration increased significantly.
“The survey, conducted in 14 Indian cities in May, shows that people are checking the mobiles at least 41 times a day,” Ritesh Chopra, Country Manager (India) of Symantec told Business Line.
About 50 percent of people have 20 apps in their phones in which about 5 are mobile wallets and e-commerce apps which they use for their business and commercial purpose. People are unwittingly giving permissions to unknown and unverified developers to download apps. A good no. of apps are fake and can steal all this information and data from your phone and can make your life miserable
There are a lot of cyber crime cases takes place nowadays in India. And half of them takes place from phones.
CONCLUSION: SO, THIS IS NECESSARY TO ONLY DOWNLOAD THOSE APPS WHOM YOU TRUST AND NOT GIVE PERMISSIONS TO UNKNOWN AND UNVERIFIED DEVELOPERS TO DOWNLOAD APPS.